Western Rifle Shooters Association
Do not give in to Evil, but proceed ever more boldly against it
- Check Your Spam Filters
- Mogambo On The Fed's Follies
- Open Source Intel Project
- The Art Of Strategic Citizenship
- Denninger: Reefer Madness
- Assassin Nation
- Fight The Premise
- The Way Things Work...Until Catastrophe
- Two For A Sunday Afternoon
- Exit Ahead
Shooting Resources
Basic Rifle Marksmanship Series
Practical Resources
The Next Steps Series
The Weapons Platform: You and Your Body
Political Resources
- Codrea's War on Guns
- Codrea's National Gun Rights Examiner
- Sipsey Street Irregulars
- Gun Owners of America
- Jews for the Preservation of Firearms Ownership
- FreeForces S2 - Gathering The Information The American Press Ignores
- Injustice Everywhere -- Daily Police Misconduct Reports
- Radley Balko's The Agitator
- Billy Beck
- New Paltz Journal
- Arctic Patriot
- John Venlet
- Ed Rasimus
- Bill St. Clair: End the War on Freedom
- Claire Wolfe's "Living Freedom"
- American Digest
- Cato Institute's Cato At Liberty Blog
- Second Amendment Patriots
- Citizens Committee For the Right to Keep and Bear Arms
- Keep & Bear Arms (RKBA news aggregator)
- Junior Deputy Accountant
- Surplusrifle.com
- Chris Muir's Day by Day
- View from the Porch
- Causapatet
- The Elector Retards
- The Liberty Sphere
- Memento Mori
- Arms and the Law
- Oleg Volk's A Human Right
- The Belmont Club
- Eternity Road
- John Robb's Global Guerrillas
- Big Fur Hat's 'I Own The World'
- Sense Of Events
- The Foundation for Economic Education
- Mish Shedlock's Global Economic Trends Analysis
- Bloomberg News
- Investor's Business Daily Editorials
- Telegraph (U.K.)
- Restore The Constitution
- The American Thinker
- Drudge Report
- Zero Hedge
- Real Clear Politics
- Real Clear Markets
- Real Clear World
- Breitbart's Big Government
- Maggie's Farm
- Instapundit
- Mises.org (Economics & Liberty)
- Michelle Malkin
- David Warren Online
- Power Line
- The People's Cube
- Chicago Boyz
- Theo Spark
- Samizdata
- Jihad Watch
- James Bovard
- Mark Steyn
- Sultan Knish
- John Batchelor
- The Cliffs of Insanity
- GardenSERF's Plot
- Free North Carolina
- Victor Davis Hanson
- Washington Rebel
- TL In Exile
- Gates of Vienna
- EU Referendum
- Autonomous Mind
- Asia Times
- Jamestown Foundation
- Pro Libertate
- Jim Sinclair's Mineset
- John Galt's Shenandoah
- Denninger's Market Ticker
- Matt Bracken's Enemies Foreign And Domestic
Links
Subscribe to
Comments [Atom]
Wednesday, December 15, 2010

30 Comments:
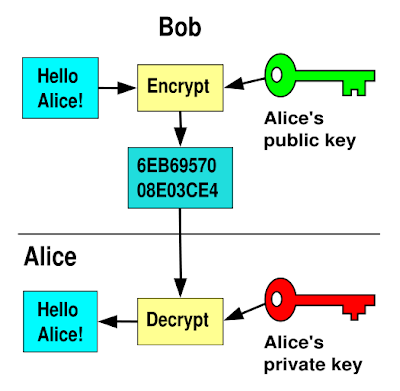
Yes but ... you have given an example of key exhange ... which do you want?
Tell you what ... drop me a line at hadavis@wispertel.net and I can explain ... your example appears to be one of public key exchange which is how encryption keys are distributed vs. just encryption.
CA: The unfortunate fact is that REAL safety is a chimera. It was proven in the '80s that it is possible to corrupt the program ("compiler") which turns source-code (programmer's work) into an executable program (what the PC runs) so that it would insert a back-door into anything it compiled.
Then there's the possibility that NSA has quantum computers - which could go through any encryption we have like a hot knife through warm butter.
Bottom line: TPTB can probably read anything we do whether encrypted or not. That said, I still think it's a worthwhile endeavor, if only to make them waste resources on people like us. No point making it easy for them.
Besides, they really don't NEED evidence - ask Olafson, as just one sad, sick example. They'll just make it up.
With all that in mind, a good option for personal encryption is "GPG4win" - which is the open-source version of PGP, specifically created for Windows users.
There's a tutorial here: http://negotiationisover.com/2010/07/pgp-for-dummies-the-tutorial/
For some reason the page isn't loading, but can be accessed through Google cache at http://webcache.googleusercontent.com/search?q=cache:7gBu0SmVHNQJ:negotiationisover.com/2010/07/pgp-for-dummies-the-tutorial/
The "guts" of said "tutorial" are:
"...
1- Download and install this software:
http://www.gpg4win.org/download.html
=> http://ftp.gpg4win.org/gpg4win-2.0.3.exe
2- Installing Gpg4win
http://gpg4win.de/handbuecher/novices_5.html
3-Creating a key pair
http://gpg4win.de/handbuecher/novices_6.html
4-Sharing the Public Key
http://gpg4win.de/handbuecher/novices_7.html
5-Decrypting an email
http://gpg4win.de/handbuecher/novices_9.html
6-Attaching a key to your key ring
http://gpg4win.de/handbuecher/novices_10.html
7- Encrypting emails
http://gpg4win.de/handbuecher/novices_11.html
..."
Alternatively, there's a .pdf file at http://wald.intevation.org/frs/download.php/775/gpg4win-compendium-en-3.0.0-beta1.pdf which contains the same basic info.
My only "gripe" with these is that though the text is in English, the pics/examples/illustrations are in German. Still, I had no trouble deciphering, especially when I followed along with the step-by-step for purposes of evaluation prior to posting here.
Anyone able to use a PC to send e-mail should -- SHOULD -- be able to work through this in a half hour or so.
The creators even provide a "practice" range with a robot which will pretend to be the "user" on the other end. This lets novices practice without confusing each other... Once they've got it down then they can start using it to talk to real, live folk...
HTH!!
DD
Dangit - my long post just got eaten.
See "novice" how-to at http://wald.intevation.org/frs/download.php/355/gpg4win-for-novices-1.0.0.pdf or HTML version at http://gpg4win.de/handbuecher/novices.html
See FULL Docs at http://wald.intevation.org/frs/download.php/744/gpg4win-compendium-de-3.0.0.pdf or HTML Version at http://www.gpg4win.org/doc/en/gpg4win-compendium.html
Program download: http://ftp.gpg4win.org/gpg4win-2.0.4.exe
Anyone capable of posting here, copying/pasting text and sending an e-mail message should be able to walk through the "novice" tutorial and be up-and-running in a half hour or so.
No kidding. The whole PGP/GPG key thing leaves my brain a pile of goo on the floor trying to get the concept.
It depends on what you want to do.
For encrypting files: http://www.gpg4win.org/
and email: http://www.mozillamessaging.com/en-US/thunderbird/
For File and Disk encryption: http://www.truecrypt.org/
Bruce Schneier has a page on how to do encryption with a deck of cards. Not public key encryption though:
http://www.schneier.com/solitaire.html
Pete,
Public/Private key crypt consists of the use of a tool used to create both a private and public key.
The private key is kept by you and the public key is given to others. The public key is used by others to encrypt something destined for you.
They will use your public key to encrypt a message and send it to you. You will use the private key to decrypt the message.
Private keys should be kept safe with physical access to them limited and password protected (password chosen when generating key pair). One way to do this is to put both the tools and public/private key on a USB memory stick and only connect it to a machine when using your tools. Can the machine be compromised thus getting your key presses for the password (yes) but the private key would have to be copied as well.
Make your keys big.
Google PGP and start getting some background on various tools wrapped around PGP these days and thoughts on what sufficient key size is given the amount of computing power out there and the number of graduate and doctorate level mathematicians hired by N ~ S - A.
the google search term you seek is "gpg tutorial".
think of public key (asymmetric) crypto as handing out locks (public key). any random sender can put one on a box and send it to the recipient - only the recipient has the (private) key.
bear in mind that you've asked how an engine works - specify what you want to accomplish (if public key doesn't cover it) and the cypherpunks among us can be of much more service.
Rhett III
Sorry for the long post, but I wanted to try and be complete with this. I know it's not an easy level read, but it's important stuff that needs to be really understood. PGP allows anyone to send and receive secure email and messages. Users can send and receive encrypted files of any sort; text, videos, documents, photos, etc. The user must install PGP desktop from the PGP website. The user is given a key, which gives the software full functionality for 30 days. After 30 days, the features that make it work automatically with Microsoft Outlook are disabled. However, the ability to encrypt and decrypt messages and files remains perpetually. Using only the functionality of the expired evaluation software, the user simply creates a file to encrypt and send as an attachment to a normal email. The recipient receives the file and decrypts it using PGP. PGP uses public key encryption, here’s how it works: Each user creates a strong passphrase, just like a password, only longer. The passphrase is secret. PGP automatically takes that passphrase and creates a “public key” to accompany it. PGP takes the public key and sends it to its server. When someone wants to send you a secure message, they download your public key from the server that anyone can access. PGP then uses your public key to encrypt a sender’s message to you. The message is sent secured. Only you have the private passphrase to decrypt the message, but anyone can use your public key to encrypt a message for you. Again; the sender encrypts a message to your public key, and you decrypt it with your private passphrase. This method is as secure as it can possibly get. No one has ever broken this method, although the government has tried continually. The message or file is encrypted at your computer, and is not decrypted until the recipient enters their passphrase on their own computer. There is no back door. And it is absolutely free. This method uses 128 bit passphrase encryption.
So it’s actually secure, and PGP maintains its tradition of having no “back door” method of decrypting your files, even for government. I highly recommend that patriot groups everywhere adopt this method for encrypted comms. Even if there is only one person who is comfortable with this per local group, the advantages can be huge for everyone. The encrypted files may also be saved to CD’s, or USB thumb drives.
Further, individual files may be encrypted with individual passphrases that will self decrypt when the passphrase is given. This has nothing to do with the public key system. Example: I want to secure a set of Word documents. I tell PGP to secure them in a self decrypting file. I am asked to enter a passphrase to encrypt the files with. I choose “12345” (an actual passphrase may contain 20 or more characters). The files are then encrypted, and are ready to be distributed at will. If the recipients are given the passphrase, they may decrypt the file, using PGP on their computer.
First though, you must get the program and install it on your machine. If there is someone in your area with computer knowledge, get them to help set you up. The full home desktop software is $100 if you want to keep the whole thing. The full version will automatically encrypt and decrypt your emails, and it does some more automatic stuff, but if you don’t need it then you may at least want to get the program and let it expire into the free version. You can do everything I’ve described with the free version.
http://www.pgp.com/downloads/desktoptrial/desktoptrial2.html
Where did Alice get her private key? Does everybody get a public key? So my supercomputer only has to guess one of the two keys?
Phil Zimmerman's ZFone http://zfoneproject.com/prod_zfone.html
is about as easy as encryption gets.
For older computer voice-comm + file exchange, PGPFone 2.0 (Win/Mac) is unsupported-yet-open-source and a great application for high-quality older PowerBook laptops with G3 processors.
Actual "security" depends on how compromised the computers and environment on either end are, and how interested and capable the evesdroppers are. The stream between terminals is likely pretty secure from brute-force decoding attack in time to be useful to the OpFor.
Short and highly secure messages are best made by random-number one-time-pad, hand delivered, and coded-decoded by hand. Don't forget about traffic analysis that does not require coded messages to be decoded to glean a good notion about number of users and general tempo of operations.
Cheers.
If you are using microsoft stuff, the following is a decent "how to" for email:
http://technet.microsoft.com/en-us/library/bb742473.aspx
This is a "why you should":
http://netsecurity.about.com/cs/emailsecurity/a/aa051004.htm
But if you need real hand-holding to install it, you will need to tell us what software you intend to use so that someone could help you.
It's called public key encryption and it's implemented using GNUPG or GPG on the open source side. It's compatible with PGP, which has been around for nearly 20 years and is extremely robust.
http://gnupg.org/
The encryption is based on what you have (the key) and what you know (a passphrase).
When you generate a set of keys you have a public key which you share (perhaps on a public key server) and a private key, which you keep to yourself.
Bob sends Alice his public key. Alice uses her private key and passphrase, and with Bob's public key decrypts the message.
It's simple, it's quick, and it's very effective.
Of course, the question is if any of that does ANY good if the Bad Guys are on your computer. Not that there are backdoors or anything in ANY software, but DOJ sure gave up easily on the Microsoft lawsuit a few years ago...
Here is a good explination of BASIC, entry level encryption.
Versus nosy neighbor type, not for nosy superpower government...
http://lifehacker.com/180878/how-to-encrypt-your-email
I am encouraged that we are discussing these issues.
I would be willing to do a test run with you if desired. Be advised, I am @ 3rd grade level as well...
Justin
I made a quick tutorial for my favorite software here...
http://rainesrebels.blogspot.com/2010/12/encryption-made-easy.html
gnupg.org has it all explained... it's actually quite easy to implement.
Hmmm...
http://market-ticker.org/akcs-www?singlepost=2314982
...
Justin
I'm not sure that diagram is even a good example of public key exchange for PGP. I am guessing you want to do email encryption using some version of Windows. I don't think there is an EASY way to explain it. I'll give a shot though.
There are basically two methods to send encrypted traffic via email. One is to use encrypted file attachments and the other is to actually encrypt the text of the email itself.
Using encrypted file attachments requires the use a common word processor program and encryption/decryption software package that both the sender and receiver have on their systems. Using this program type up a message and save it to a file. Get and Install your favorite file encryption/decryption software package [there are several out there], and encrypt the file using either the Blowfish or Twofish encryption algorithm at a 256 bit length. I would use a long passphrase, something over 15 characters and use numbers and special characters ie $#^&* in the passphrase. Attach it to an email and send to a reciever who also has the same encryption/decryption software. THE PROBLEM. You will have to give the receiver(s) the "passprhrase" used to encrypt and also decrypt the file. One can not simply send the passphrase in the clear in the email. Sort of defeats the purpose of encryption. So you will need a "covert/secure" way to distribute the passphrase to the intended recipients. This type of encryption has the potential for being the hardest to crack but also the hardest to implement because of distributing the passphrase to the people who need to decrypt your attachment and encrypt a reply. Security of the passphrase is the probably the weakest part of this scheme.
The second method is to use either PGP or GPG plugins to your email client software, i.e. the software you use to send email. You can get PGP at http://www.pgp.com/products/ and you can get GPG packages for windows at http://www.gnupg.org/ Ensure it is compatible with your email software. Both packages will generate a public key and a private key. In order to get two way encrypted email with someone you need to get their public key and you will need to give them your public key. Both persons should be using the same algorithm and bit length. Once you have verified the receiver and his public key, he will need do the same for you. Then you simply type up an email and select, usually from a pull down menu or bar button, to encrypt it when you send it. IF you have someone's public key and receive encrypted traffic then you should also have a pull down menu item or toolbar button to decrypt it.
Ok that's as simple as I can make it and I left out some of the details of PGP/GPG. I hope this helps.
Dedicated Dad writes:
"The unfortunate fact is that REAL safety is a chimera."
Safety vs. convenience is a tradeoff which cannot be avoided.
"Then there's the possibility that NSA has quantum computers - which could go through any encryption we have like a hot knife through warm butter."
EXCEPT encryption which is based on one-time pads. A USB drive is a fine way to transport a pad.
"Bottom line: TPTB can probably read anything we do whether encrypted or not."
Nevertheless, there is still merit in not leaving your keys in your car with the windows rolled down. In a movie plot, the national intelligence services can pin you down like a butterfly. In reality, anything that raises the cost for crooks lowers the total amount of crookedness occurring. In the movies, one droplet of supervirus kills all the humans outside airtight bunkers. In reality, several envelopes of weaponized anthrax were sent through the mail, and only a dozen people died. Don't be scared by movie-plot public relations. If you can learn the nerdiness behind long-range shooting, then you can handle GPG and Linux. It's just a technical field. Pick a tasty-looking corner, take a few bites, and chew on them.
"With all that in mind, a good option for personal encryption is "GPG4win" - which is the open-source version of PGP, specifically created for Windows users."
Nope, Windows is going to be full of infections, remotely controlled by heaven knows who. If you insist on using Windows, than don't bother encrypting anything.
For the Market Ticker post below Denniger misses where and how super gov would listen to traffic and or mirror it.
Imagine that all switch and router providers where forced/encouraged to include code that would allow for the replication of traffic going in and out of a particular switch (think the big pipes) via a SPAN Port. It's trivial.
I worked for a company that analyzes a massive amount of DNS traffic and looks for trends, denial of service attacks, outages via SPAN Port analysis with open source tools like libpcap.
So there is that which is probably used to cull through massive amounts of data (think carnivore), but for the rest of the ... the risks are in what some other posts stated regarding how secure are your machine(s)? Who do you contact whether the payload is secure or not? Who contacts you? What do you buy? What do you post online? What magazines do you subscribe to? What kind of music do you listen to? What is your credit score? Are you single or married? Kids? For the posts online all contact images can be easily stored with facial recognitions software used against them and then...
From this relationships can be visualized and extrapolated. Tools like this are a good example: http://www.visualcomplexity.com/vc/project.cfm?id=367 Instead of music/song characteristics, human demographic patterns can be used.
Another buddy of mine did this for a large bank and was able to find patterns between different online accounts and thus pin them to certain people that had committed fraud.
The example is NOT of a key exchange, it's an example of using a Public Key to encrypt a message from Bob to Alice that only Alice can decrypt using her Private Key.
When you use PGP (Pretty Good Privacy) you generate a Key-Pair, the Public Key you can give to anyone or post in public and the Private Key you keep secret and use to decrypt messages created with the Public Key. Bob can post the encrypted message in public and only Alice can decrypt it.
You can also use the Key-Pair in reverse - you can encrypt a message using your Private Key, that anyone can decrypt using your Public Key which provides "Authentication" - only YOU could have created the message.
Used in conjunction, the message can be encrypted with your Private Key first, and then that message encrypted with someone else's Public Key. They use their Private Key to decrypt the message that only they can, and then use your Public Key to verify that only YOU could have sent it.
Pretty Good Privacy :-)
BTW - the FedGov dropped their lawsuit against Phil Zimmerman after the publication of PGP Version 2.6.2, so later versions can be considered to be "compromised". You can get MSDOS versions that you can run in a command window of PGP 2.6.2 from MIT - Google for it :-)
The example is NOT of a key exchange, it's an example of using a Public Key to encrypt a message from Bob to Alice that only Alice can decrypt using her Private Key.
When you use PGP (Pretty Good Privacy) you generate a Key-Pair, the Public Key you can give to anyone or post in public and the Private Key you keep secret and use to decrypt messages created with the Public Key. Bob can post the encrypted message in public and only Alice can decrypt it.
You can also use the Key-Pair in reverse - you can encrypt a message using your Private Key, that anyone can decrypt using your Public Key which provides "Authentication" - only YOU could have created the message.
Used in conjunction, the message can be encrypted with your Private Key first, and then that message encrypted with someone else's Public Key. They use their Private Key to decrypt the message that only they can, and then use your Public Key to verify that only YOU could have sent it.
Pretty Good Privacy :-)
BTW - the FedGov dropped their lawsuit against Phil Zimmerman after the publication of PGP Version 2.6.2, so later versions can be considered to be "compromised". You can get MSDOS versions that you can run in a command window of PGP 2.6.2 from MIT - Google for it :-)
Once again, Don K. is accurate ONLY IF neither the computer belonging to the sender nor the computer belonging to the recipient is compromised. The DOJ had an adjudication against Microsoft showing they broke the law, and the case was in the penalty phase with reasonable remediations proposed. The DOJ suddenly gave the case away and let Microsoft escape without any meaningful penalties or controls against future excess. Sort of like a precursor to the Black Panther terrorists at the polling place. Read what you want into that, but as for me if EITHER sender or recipient is using a Microsoft machine, the content might as well be plain text unencrypted.
If you are TRULY concerned about ComSec for your communications, DO NOT use a Microsoft box. Apple? I don't know. Linux would seem to be the OS of choice for security. And it should work well for anything you really care to do securely, with the readily available apps for it.
I should probably add that a dual-boot box (Windows and Linux) is not smart if you have unencrypted data on the Linux partition, since there are apps that can readily read "ext" partitions from within Windows, even if Microsoft does not let you do that natively. Either encrypt your data (and your ALL your keys) so that they cannot be read from the Windows partition, or better yet run a Linux-only box, and DON'T "share" its partitions, folders, or files.
And an additional perspective:
http://www.dailytech.com/article.aspx?newsid=20424
When even THEY are convinced their systems will be compromised, why would YOU presume that yours will not? ESPECIALLY given the funds and resources disparities.
And yet one more for your consideration:
http://www.dailytech.com/Whitelisting+Ban+Those+Naughty+Devices+and+Beef+up+Security/article20380.htm
Re: Mark Matis
Fair enough ...
If the spooks are in your machine, all bets are off :-)
Good:
http://www.youtube.com/thetorproject#p/a/u/1/KgWV7rSCK-s
Better:
http://sourceforge.net/projects/anonym-os/
Post a Comment
Subscribe to Post Comments [Atom]
<< Home